The Unarchiver Password Cracker
Although increased internet connection speeds mean that web users have to worry far less about the size of the files they download, a large proportion of files are delivered in one compressed format or another. There are a number of different formats to choose from including ZIP and RAR, but many others also exist.
OS X includes built in support for the decompression of a number of popular archive formats, but The Unarchiver extends the supported number of file types much further and adds a number of useful options that make the process of decompressing much easier.

The outdated version of The Unarchiver that came installed by default on earlier versions of macOS do not support 7zip with passwords. However, The Unarchiver has supported encrypted 7zip files for some time. Delete the old version, and install the current version, and you will be good to go, just as @Cezary suggests. – Lexible Jan 6 at 22:31. The Unarchiver is able to automatically join together split archive - such as those with.001,.002,.003 extensions - and the number of support formats is staggering. All of the popular formats are supported as well as older and more obscure file types.
The Unarchiver is able to automatically join together split archive - such as those with .001, .002, .003 extensions - and the number of support formats is staggering. All of the popular formats are supported as well as older and more obscure file types.
Once you have installed the application, all that is left to do is to indicate which files types it should be allowed to handle. The Unarchiver is likely to quickly turn out to be one of those tools you use on an almost daily basis.
What's new in 4.0?
- New icon is here.
- UI was given a makeover: we leveled every string of text and measured every indent.
- Localizations were meticulously checked, fixed and then checked again. BTW, did you find an error? Tell our support and we'll fix it right away.
- Speed was improved. You can now get the contents of the archive you’ve just downloaded much much faster.
Verdict:
A virtually flawless way to extract the contents of a huge number of different compressed file formats.
/! This is for educational purposes only, and should not be used for unauthorized access, tampering or accessed illegally without owner permission.
This page will help you to retrieve/extract the hash associated to an OSX account. We tried to enumerate all the OS X flavors available, but this article is still 'in beta' depending on the new OS X versions.
Once the hash is extracted, you can send it here and we will try to recover it.

The same as in 10.2 (Jaguar). See below.
OS X 10.1 (Puma)
The same as in 10.2 (Jaguar). See below.
The Unarchiver Password Crackers
Dump the hash :
This hash is created using the Unix DES Crypt(3) function, where the password is first truncated to 8 characters.
OS X 10.3 (Panther)
First find out a users' GUID:
Next take that GUID and dump the hash file
The first 64 characters are the NTLM hash (first 32 NT, next 32 LM) and the last 40 characters are the SHA1 hash.
You can obtain the GUID just as in 10.3 (Panther). See above.
After obtaining the GUID, you can dump the passwords just as in 10.5 (Leopard). See below.
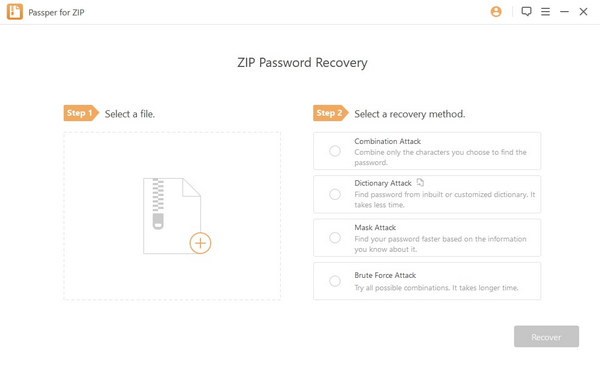


OS X 10.5 (Leopard) + OS X 10.6 (Snow Leopard)
First find a users' GUID:
After getting the GUID you can dump various hashes. By default the only hash stored is the salted SHA1. If the user has turned on SMB file sharing then the NTLM hash will also be stored.
If you upgraded from 10.3->10.4->10.5 then the zero salted SHA1 is also stored.
Salted SHA1 (first 8 characters are the salt)
Zero-Salted SHA1 (first 8 characters are the salt and will always be all zeros)
NTLM (first 32 characters are NT, next 32 are LM)
Use this tutorial
OS X 10.8 (Mountain) & 10.9 (Mavericks) & 10.10 (Yosemite)
The shadow files are stored on the filesystem at /var/db/dslocal/nodes/Default/users/%user%.plist.
They are in plist format so you'll need to use the plutil command to view them or use the defaults command to extract/write specific keys if desired.
Only the root user has access to the files.
To view the contents of a shadow file for a user: To get the hash: Where %username% in the above example is the user you're looking for the hash for.
Finally the wanted hash starts with '$ml$' and length is 203 characters.
Few links to help you :
- http://lionsurf.wordpress.com/crack-user-password-in-os-x-mountain-lion/
- http://www.michaelfairley.co/blog/2014/05/18/how-to-extract-os-x-mavericks-password-hash-for-cracking-with-hashcat/
- script to automate the process (.app).
The hashes of the users are stored in: To get the hash: or directly through directory services:
Tool to automate these steps
Davegrohl tool created in early 2011 is a password hash extractor & companion tool to John the Ripper.
Sadly the development of this tool has been stopped (but could be forked..), the current status is :
Dave compiles fine on Yosemite and will happily (but very slowly) crack user passwords. Out of the box, OS X uses PBKDF2 to encrypt its user passwords which is very slow to crack for one machine. Turning on Windows (SMB) file sharing will disable this feature.